As we see in part 2, the guided deployment created four things for us, let’s look into what and why.
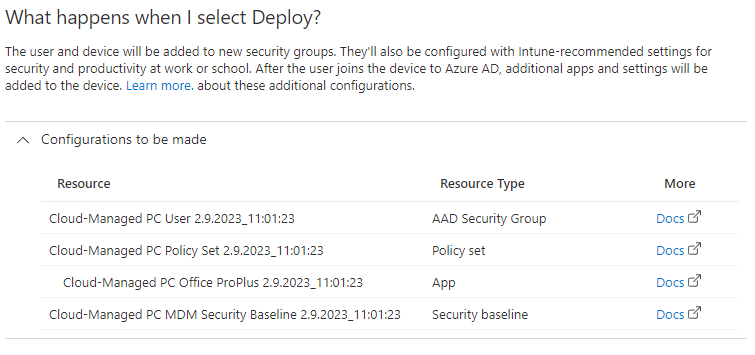
AAD Security Group
You can find this under endpoint.microsoft.com ➡️ Groups.
“Security groups are used to give group members access to applications, resources and assign licenses. Group members can be users, devices, service principals, and other groups.”
When working in Azure AD we try to group everything in groups and then adding the groups to functions. This simplifies administration later down the line and makes it possible to standardize implementation. The more users you have, the more important it is.
🎓 Golder rule: Always add users to groups and groups to policies.
💡 When using security groups, it’s important to have a name standard and work with a plan. This is a generated group name, but we’ll leave it for now.
Read more on Microsoft Learn.
Policy set
You can find this under endpoint.microsoft.com ➡️ Devices ➡️ Policy sets.
Policy sets is as the name suggests a several policies in one package and we use this to simplify deployment. A set can include Application to install, configurations and protection, Device configuration and compliance as well as Enrollment profiles and status pages.
In my policy set it only included the app (see below)
Read more on Microsoft Learn .
App
You can find this under endpoint.microsoft.com ➡️ Apps ➡️ Windows
A fresh install of Windows doesn’t include the Microsoft Office package. This will install Microsoft Office 365 ProPlus on the PC. This includes Outlook, Work, Excel, PowerPoint and OneNote.
🔎 If you open the policy you can see under Properties that it uses Assignments via policy sets (see above).
Note: Microsoft Office 365 ProPlus has been renamed to Microsoft 365 Apps for enterprise and often referred to as Microsoft 365 Apps.
Read more on Microsoft Learn.
Security baseline
You can find this under endpoint.microsoft.com ➡️ Endpoint security ➡️ Security baselines.
A security baseline is a set of security settings we apply to a device. This can be BitLocker, Browser settings, Password requirements, Firewall settings and much much more. You can see a list over settings here.
Read more on Microsoft Learn.
⚠️ Working with security baseline policies are an important part of intune, the recommended settings might be too strict and not suitable for your organization. I don’t recommend the defaults for SMB, but for this test we will use them.
